Using Nginx as a Reverse Proxy for Elastic Stack
Prerequisites⌗
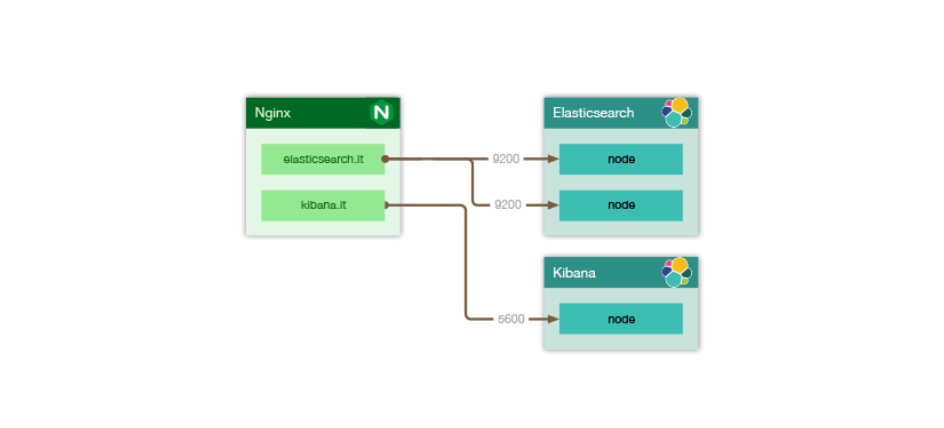
Assume that Elasticsearch and Kibana have been successfully deployed using Docker. If you haven’t deployed them yet, you can refer to the blog posts “Elastic Stack - Elasticsearch” and “Elastic Stack - Kibana”.
Note: The Nginx container needs to be in the same network as Elasticsearch and Kibana.
Nginx Configuration Files⌗
Elasticsearch⌗
server {
listen 80;
server_name elasticsearch.example.com;
return 308 https://$host$request_uri;
}
server {
listen 443 ssl http2;
server_tokens off;
server_name elasticsearch.example.com;
ssl_certificate /etc/nginx/cert/fullchain.cer;
ssl_certificate_key /etc/nginx/cert/example.com.key;
# Recommendations from https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_ciphers '!aNULL:kECDH+AESGCM:ECDH+AESGCM:RSA+AESGCM:kECDH+AES:ECDH+AES:RSA+AES:';
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
# disable any limits to avoid HTTP 413 for large image uploads
client_max_body_size 0;
# required to avoid HTTP 411: see Issue #1486 (https://github.com/docker/docker/issues/1486)
chunked_transfer_encoding on;
add_header Strict-Transport-Security max-age=15768000;
# OCSP Stapling ---
# fetch OCSP records from URL in ssl_certificate and cache them
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/nginx/cert/ca-bundle.trust.crt;
location / {
proxy_pass http://elasticsearch:9200;
proxy_set_header Host $host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings.
proxy_set_header X-Forwarded-Proto $scheme;
proxy_buffering off;
proxy_request_buffering off;
auth_basic "Please sign in elasticsearch";
auth_basic_user_file /etc/nginx/auth/elasticsearch;
autoindex on;
}
}
Kibana⌗
server {
listen 80;
server_name kibana.example.com;
return 308 https://$host$request_uri;
}
server {
listen 443 ssl http2;
server_tokens off;
server_name kibana.example.com;
ssl_certificate /etc/nginx/cert/fullchain.cer;
ssl_certificate_key /etc/nginx/cert/example.com.key;
# Recommendations from https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_ciphers '!aNULL:kECDH+AESGCM:ECDH+AESGCM:RSA+AESGCM:kECDH+AES:ECDH+AES:RSA+AES:';
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
# disable any limits to avoid HTTP 413 for large image uploads
client_max_body_size 0;
# required to avoid HTTP 411: see Issue #1486 (https://github.com/docker/docker/issues/1486)
chunked_transfer_encoding on;
add_header Strict-Transport-Security max-age=15768000;
# OCSP Stapling ---
# fetch OCSP records from URL in ssl_certificate and cache them
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/nginx/cert/ca-bundle.trust.crt;
location / {
proxy_pass http://kibana:5601;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# When setting up Harbor behind other proxy, such as an Nginx instance, remove the below line if the proxy already has similar settings.
proxy_set_header X-Forwarded-Proto $scheme;
proxy_buffering off;
proxy_request_buffering off;
}
}
After completing the configuration, restart the Nginx container, or to be safe, enter the container to test if the configuration file can be loaded:
$ nginx -t
$ nginx -s reload
Then when you access Elasticsearch, you’ll find that authentication is now required.
I hope this is helpful, Happy hacking…