Traefik Proxy Implementation Based on Service Auto-Discovery
Introduction⌗
Traefik is a proxy server developed in Go language, and also serves as a Kubernetes Ingress, so it naturally supports multiple service discovery mechanisms:
- File
- Nomad
- Docker
- Kubernetes
- Etcd
- Consul
- Redis
- HTTP
- ZooKeeper
Here I mainly use Docker for automatic backend service discovery and reverse proxy!
Prerequisites⌗
I plan to use *.service.local as the access domain name for Traefik’s reverse proxy backend services, while the Traefik Console will be ingress.service.local.
Generate Certificate⌗
In the local development environment, I also want to manage and access Traefik via HTTPS, so I created a self-signed certificate using mkcert.
mkcert -cert-file ./fullchain.cer -key-file ./fullchain.key service.local "*.service.local"
Configure TLS⌗
global:
checkNewVersion: true
sendAnonymousUsage: true
serversTransport:
insecureSkipVerify: true
tls:
options:
default:
sniStrict: true
minVersion: VersionTLS12
maxVersion: VersionTLS13
cipherSuites:
- TLS_AES_128_GCM_SHA256
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
certificates:
- certFile: /certs/fullchain.cer
keyFile: /certs/fullchain.key
I found that serversTransport.insecureSkipVerify doesn’t seem to work, because a certain backend service uses a self-signed certificate to run HTTPS services. Even with this configuration item enabled, it still cannot be accessed normally. I need to manually add the --serverstransport.insecureskipverify=true parameter when starting Traefik for it to work as expected!
Orchestration⌗
services:
traefik:
image: traefik:latest
hostname: traefik
container_name: traefik
ports:
- "0.0.0.0:80:80/tcp"
- "0.0.0.0:443:443/tcp"
networks:
- traefik
command:
- --api=true
- --api.dashboard=true
- --log.level=FATAL
- --serverstransport.insecureskipverify=true
- --entrypoints.http.address=:80
- --entrypoints.https.address=:443
- --providers.file=true
- --providers.file.watch=true
- --providers.file.directory=/etc/traefik/config
- --providers.file.debugloggeneratedtemplate=true
- --providers.docker=true
- --providers.docker.watch=true
- --providers.docker.network=traefik
- --providers.docker.useBindPortIP=false
- --providers.docker.endpoint=unix:///var/run/docker.sock
labels:
- traefik.enable=true
- traefik.docker.network=traefik
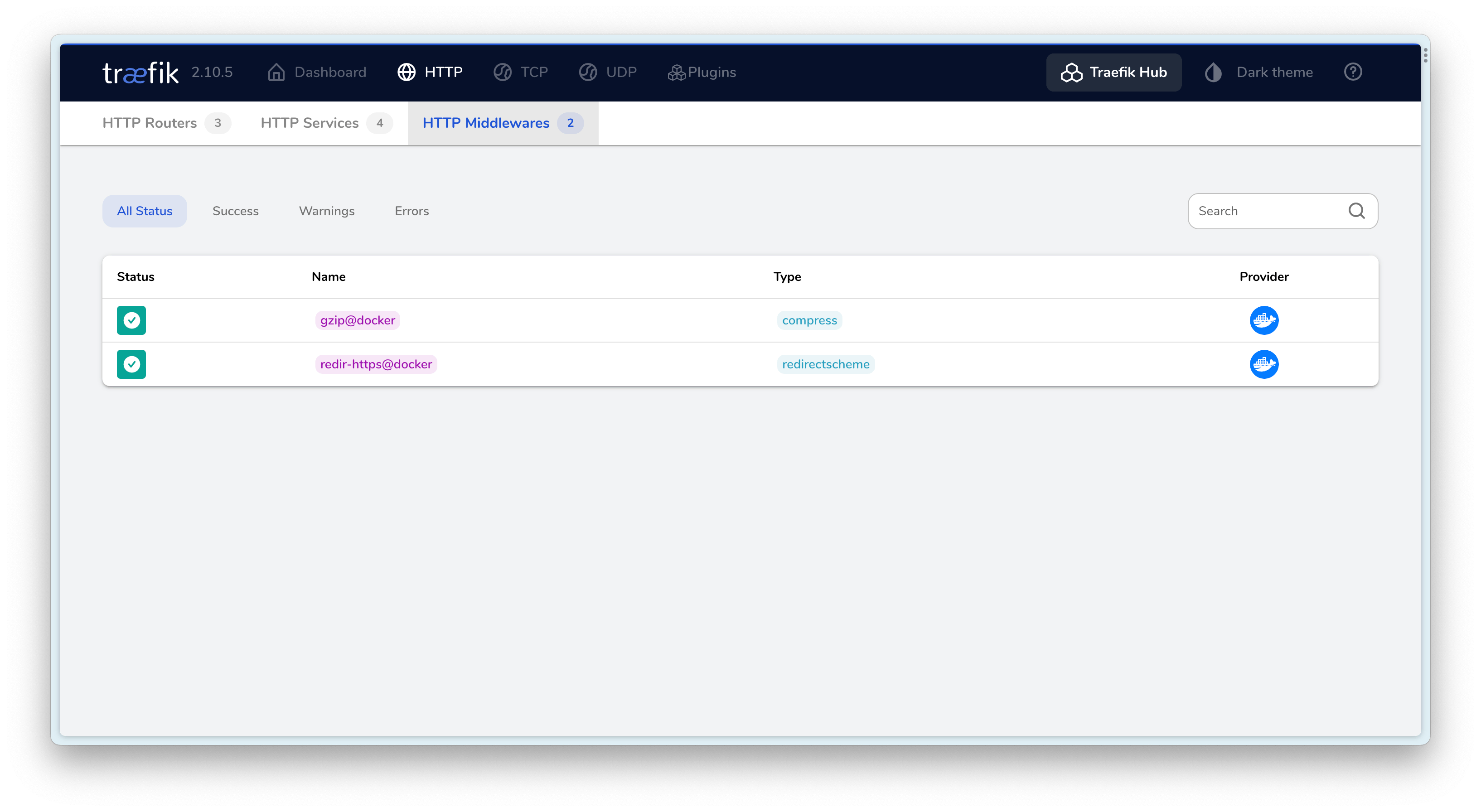
- traefik.http.middlewares.gzip.compress=true
- traefik.http.middlewares.redir-https.redirectscheme.scheme=https
- traefik.http.middlewares.redir-https.redirectscheme.permanent=true
- traefik.http.routers.traefik-dashboard.middlewares=redir-https@docker
- traefik.http.routers.traefik-dashboard-secure.middlewares=gzip@docker
- traefik.http.routers.traefik-dashboard-api-secure.middlewares=gzip@docker
- traefik.http.routers.traefik-dashboard.entrypoints=http
- traefik.http.routers.traefik-dashboard.rule=Host(`ingress.service.local`)
- traefik.http.routers.traefik-dashboard.service=noop@internal
- traefik.http.routers.traefik-dashboard-secure.entrypoints=https
- traefik.http.routers.traefik-dashboard-secure.tls=true
- traefik.http.routers.traefik-dashboard-secure.rule=Host(`ingress.service.local`)
- traefik.http.routers.traefik-dashboard-secure.service=dashboard@internal
- traefik.http.routers.traefik-dashboard-api-secure.entrypoints=https
- traefik.http.routers.traefik-dashboard-api-secure.tls=true
- traefik.http.routers.traefik-dashboard-api-secure.rule=Host(`ingress.service.local`) && PathPrefix(`/api`)
- traefik.http.routers.traefik-dashboard-api-secure.service=api@internal
volumes:
- ./certs/:/certs/:ro
- ./config/:/etc/traefik/config/:ro
# So that Traefik can listen to the Docker events
- /var/run/docker.sock:/var/run/docker.sock
networks:
traefik:
external: true
Configuration explanation:
- Line 17 sets to skip validation of backend HTTPS
- Line 36 is used to configure the gzip middleware for compressing internal response content
- Lines 37-38 are used to configure HTTP redirection to HTTPS
- Line 44 configures the Entrypoint for Traefik Dashboard as HTTP, which means it listens to traffic on port 80
- Line 45 configures the routing rule for Traefik Dashboard, which routes to Traefik when the request domain is
ingress.service.local - Line 46 specifies the backend service for Traefik Dashboard, where noop@internal is a “magic variable” internal to Traefik
Create Network⌗
docker network create traefik --subnet 10.8.10.0/24 --gateway 10.8.10.1
The subnet and gateway can be set according to your own needs!
Start Service⌗
docker compose up -d
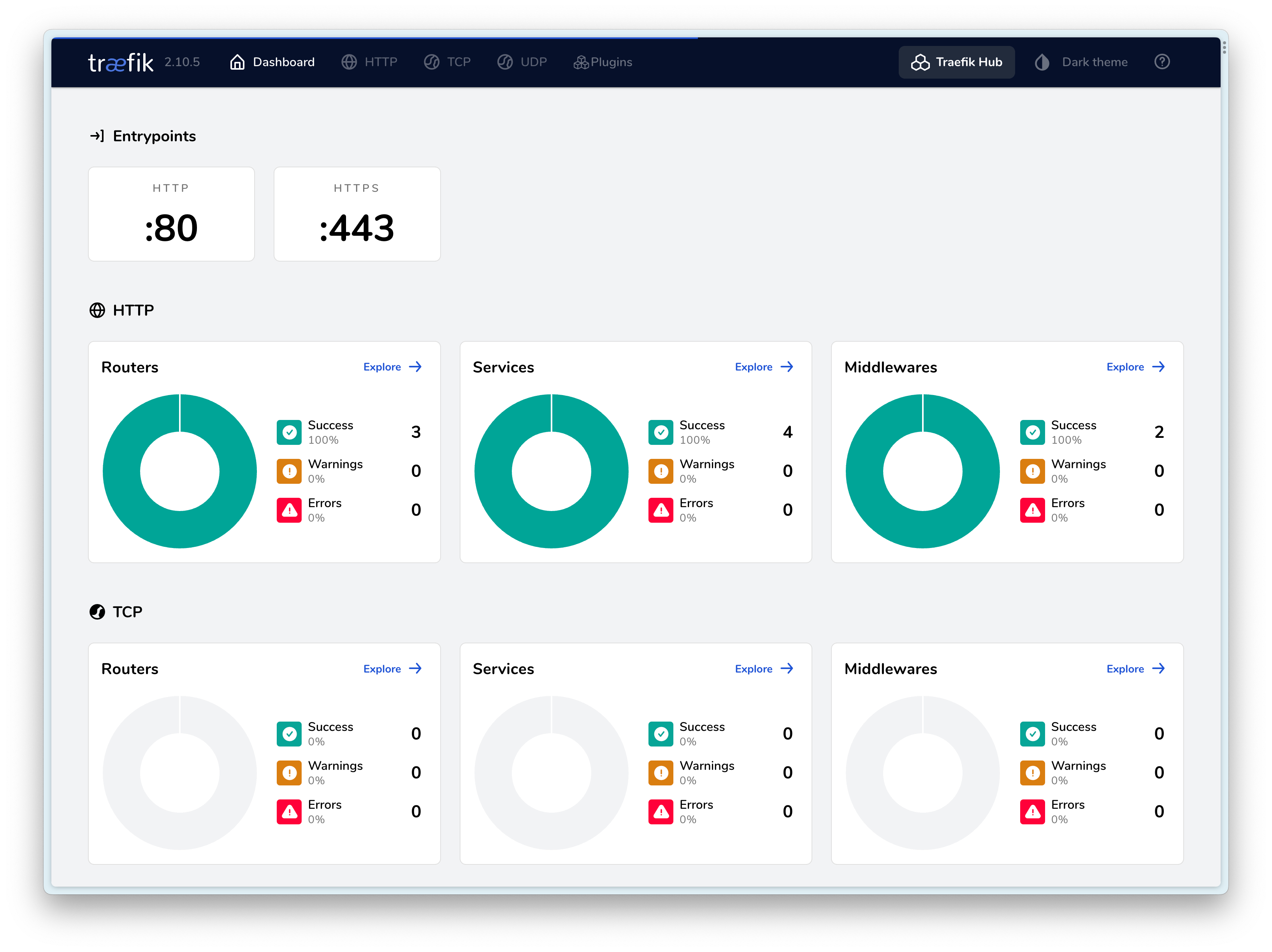
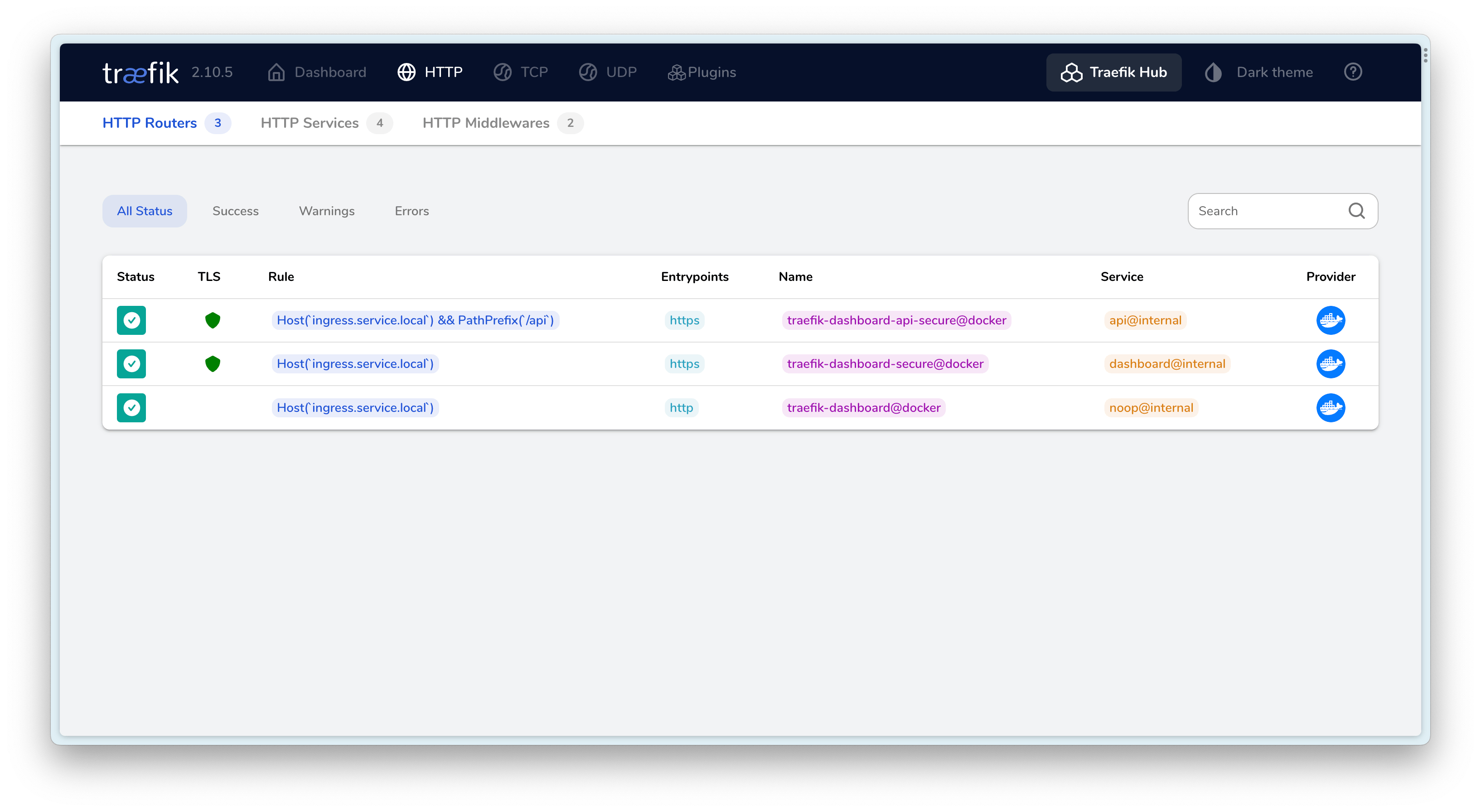
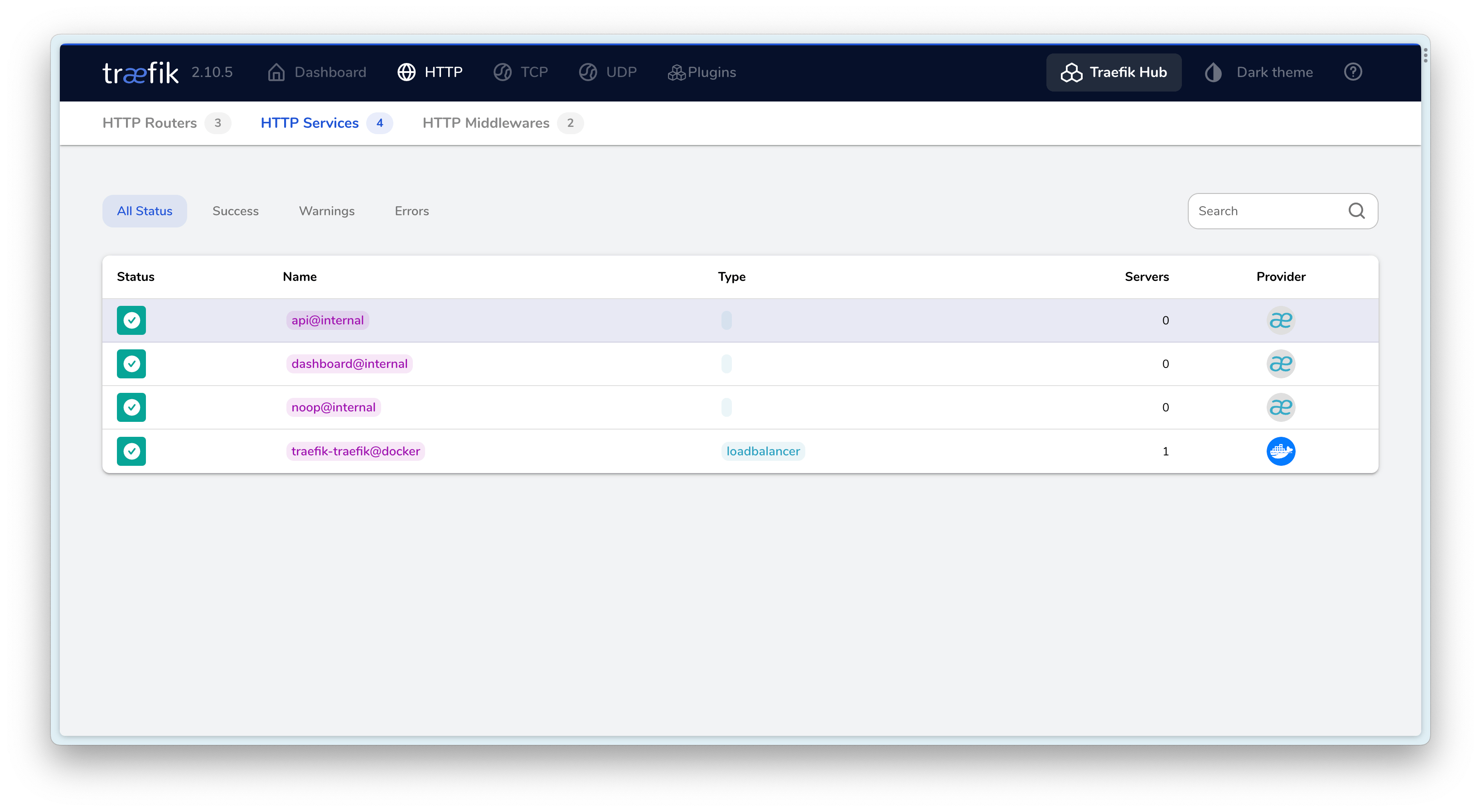
Final Result⌗
I hope this is helpful, Happy hacking…