基于 Traefik 服务发现为 Zitadel 代理

前言⌗
使用 Traefik 做代理的好处就不用我多说了,接下来直接上编排配置。
服务编排⌗
Zitadel 的其他设置可以参考官方的默认 steps.yaml,以及默认的全局配置文件 defaults.yaml。
docker-compose.yaml 文件配置如下:
services:
zitadel:
image: ghcr.io/zitadel/zitadel:latest
labels:
- traefik.enable=true
- traefik.http.middlewares.gzip.compress=true
- traefik.http.middlewares.cors.headers.accesscontrolallowmethods=GET,OPTIONS,PUT,POST
- traefik.http.middlewares.cors.headers.accesscontrolallowheaders=*
- traefik.http.middlewares.cors.headers.accesscontrolalloworiginlist=*
- traefik.http.middlewares.cors.headers.accesscontrolmaxage=100
- traefik.http.middlewares.cors.headers.addvaryheader=true
- traefik.http.routers.zitadel.rule=Host(`zitadel.local`)
- traefik.http.routers.zitadel.service=zitadel
- traefik.http.routers.zitadel.entrypoints=http
- traefik.http.routers.zitadel.middlewares=redir-https@docker
- traefik.http.services.zitadel.loadbalancer.server.port=8080
- traefik.http.services.zitadel.loadbalancer.server.scheme=h2c
- traefik.http.routers.zitadel-secure.tls=true
- traefik.http.routers.zitadel-secure.rule=Host(`zitadel.local`)
- traefik.http.routers.zitadel-secure.service=zitadel
- traefik.http.routers.zitadel-secure.entrypoints=https
- traefik.http.routers.zitadel-secure.middlewares=gzip@docker
- traefik.http.routers.zitadel-secure.middlewares=cors@docker
restart: always
networks:
- traefik
command: start-from-init --masterkeyFromEnv --tlsMode external
hostname: zitadel
container_name: zitadel
environment:
- ZITADEL_LOG_LEVEL=info
- ZITADEL_MASTERKEY=ZQ0rISokQb0o05LvTwWYyt4z32n82wVv
- ZITADEL_EXTERNALPORT=443
- ZITADEL_EXTERNALSECURE=true
- ZITADEL_EXTERNALDOMAIN=zitadel.local
- ZITADEL_FIRSTINSTANCE_ORG_NAME=BETTERDE
- ZITADEL_FIRSTINSTANCE_ORG_HUMAN_USERNAME=developer
- ZITADEL_FIRSTINSTANCE_ORG_HUMAN_PASSWORD=Developer@2023
- ZITADEL_DEFAULTINSTANCE_ORG_NAME=ZITADEL
- ZITADEL_DEFAULTINSTANCE_INSTANCENAME=ZITADEL
- ZITADEL_OIDC_DEFAULTIDTOKENLIFETIME=24h
- ZITADEL_OIDC_DEFAULTACCESSTOKENLIFETIME=24h
- ZITADEL_DATABASE_COCKROACH_HOST=cockroachdb
- ZITADEL_DATABASE_COCKROACH_USER_SSL_MODE=verify-full
- ZITADEL_DATABASE_COCKROACH_USER_SSL_KEY=/certs/client.zitadel.key
- ZITADEL_DATABASE_COCKROACH_USER_SSL_CERT=/certs/client.zitadel.crt
- ZITADEL_DATABASE_COCKROACH_USER_SSL_ROOTCERT=/certs/ca.crt
- ZITADEL_DATABASE_COCKROACH_USER_USERNAME=zitadel
- ZITADEL_DATABASE_COCKROACH_USER_PASSWORD=u1mXuweLhw4tHvMZtoOtzy0kSqYdJUea
- ZITADEL_DATABASE_COCKROACH_ADMIN_SSL_MODE=verify-full
- ZITADEL_DATABASE_COCKROACH_ADMIN_SSL_KEY=/certs/client.root.key
- ZITADEL_DATABASE_COCKROACH_ADMIN_SSL_CERT=/certs/client.root.crt
- ZITADEL_DATABASE_COCKROACH_ADMIN_SSL_ROOTCERT=/certs/ca.crt
- ZITADEL_DATABASE_COCKROACH_ADMIN_USERNAME=root
- ZITADEL_DATABASE_COCKROACH_ADMIN_PASSWORD=75bdUlVrVFcNQhmSaLhnYfIatU2dsXL9
- ZITADEL_DEFAULTINSTANCE_DOMAINPOLICY_SMTPSENDERADDRESSMATCHESINSTANCEDOMAIN=false
- ZITADEL_DEFAULTINSTANCE_OIDCSETTINGS_IDTOKENLIFETIME=24h
- ZITADEL_DEFAULTINSTANCE_OIDCSETTINGS_ACCESSTOKENLIFETIME=24h
volumes:
- cockroachdb-certs:/certs:ro
depends_on:
cockroachdb:
condition: service_healthy
cockroachdb:
image: cockroachdb/cockroach:latest
labels:
- traefik.enable=true
- traefik.http.middlewares.gzip.compress=true
- traefik.http.routers.cockroachdb.rule=Host(`cockroachdb.service.local`)
- traefik.http.routers.cockroachdb.service=cockroachdb
- traefik.http.routers.cockroachdb.entrypoints=http
- traefik.http.routers.cockroachdb.middlewares=redir-https@docker
- traefik.http.services.cockroachdb.loadbalancer.server.port=8080
- traefik.http.services.cockroachdb.loadbalancer.server.scheme=https
- traefik.http.services.cockroachdb.loadbalancer.passhostheader=true
- traefik.http.routers.cockroachdb-secure.tls=true
- traefik.http.routers.cockroachdb-secure.rule=Host(`cockroachdb.service.local`)
- traefik.http.routers.cockroachdb-secure.service=cockroachdb
- traefik.http.routers.cockroachdb-secure.entrypoints=https
- traefik.http.routers.cockroachdb-secure.middlewares=gzip@docker
restart: always
networks:
- traefik
command: start-single-node --advertise-addr cockroachdb
hostname: cockroachdb
container_name: cockroachdb
volumes:
- cockroachdb-data:/cockroach/cockroach-data:rw
- cockroachdb-certs:/cockroach/certs:rw
environment:
- COCKROACH_USER=zitadel
- COCKROACH_PASSWORD=u1mXuweLhw4tHvMZtoOtzy0kSqYdJUea
- COCKROACH_DATABASE=zitadel
healthcheck:
test: ["CMD", "curl", "-k", "-f", "https://localhost:8080/health?ready=1"]
interval: '10s'
timeout: '30s'
retries: 5
start_period: '20s'
volumes:
cockroachdb-data:
external: true
cockroachdb-certs:
external: true
networks:
traefik:
external: true
配置说明:
- 7~11 行:主要是允许跨域,这样如果有些服务在登录页面需要使用 Zitadel 的 Logo 作为标识的话,就不会出现跨域问题;
- 13~16 行:设置 HTTP 的路由以及重定向到 HTTP 中间件;
- 18~19 行:配置流量转发端口以及使用的协议,因为 Zitadel 支持 gRPC,所以这里将协议设置为 h2c;
- 21~26 行:设置 HTTPS 路由
- 30 行:–masterkeyFromEnv 从环境变量中获取 master key,–tlsMode external 仅为使用代理并开启 HTTPS 时使用
- 35 行:master key
- 37~39 行:设置外部访问端口和域名
- 41~43 行:设置第一个实例的组织名称和用户名密码
- 51~63 行:设置 cockroachdb 的数据库连接,我这里使用了 SSL
- 81~84 行:为 cockroachdb 管理后台设置 HTTP 路由并重定向到 HTTPS
- 86~88 行:为 指定上游端口和协议
- 90~94 行:为 cockroachdb 管理后台设置 HTTPS 路由
- 121~123 行:使用外部 Traefik 的网络
启动服务⌗
docker compose up -d
最终效果如下:
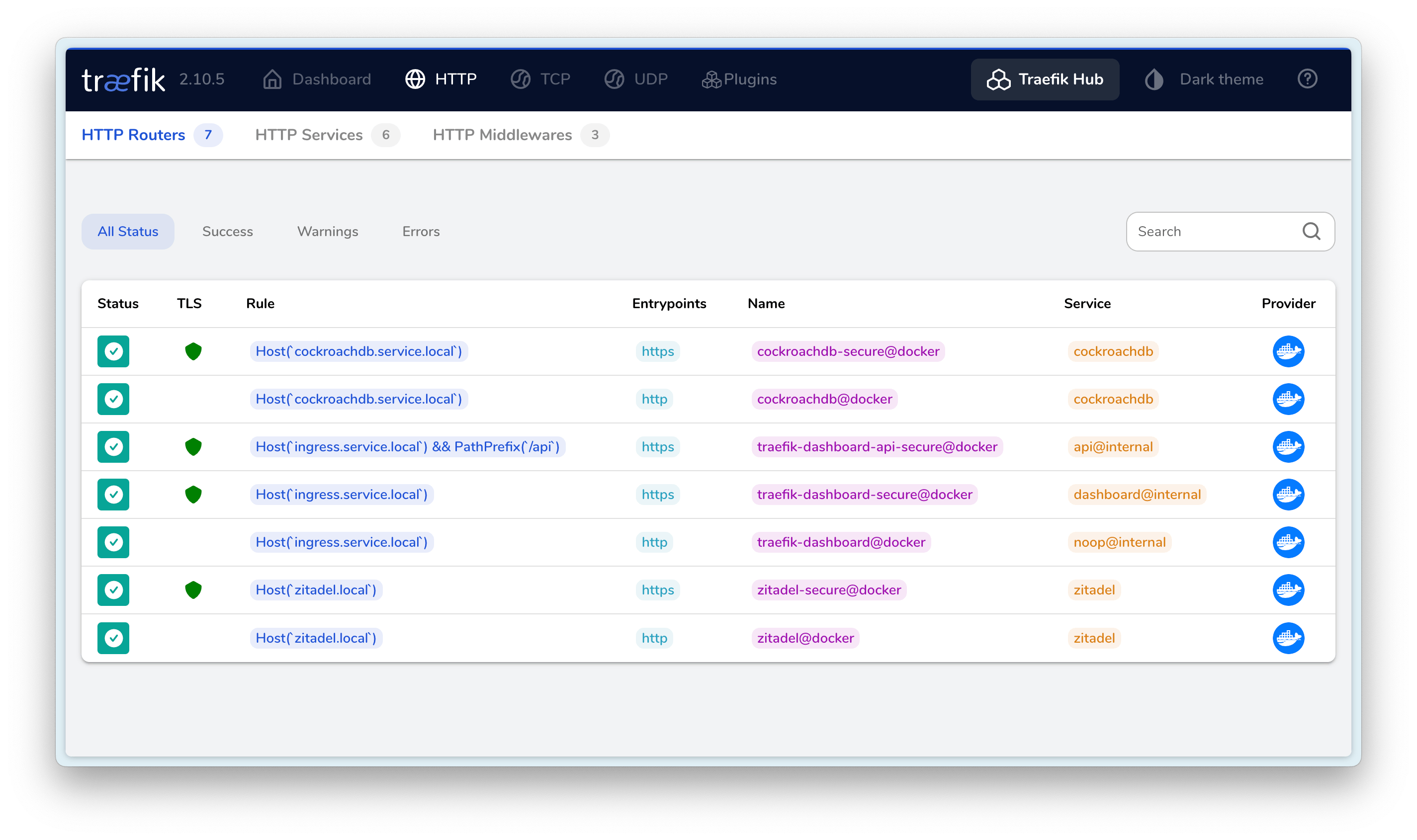
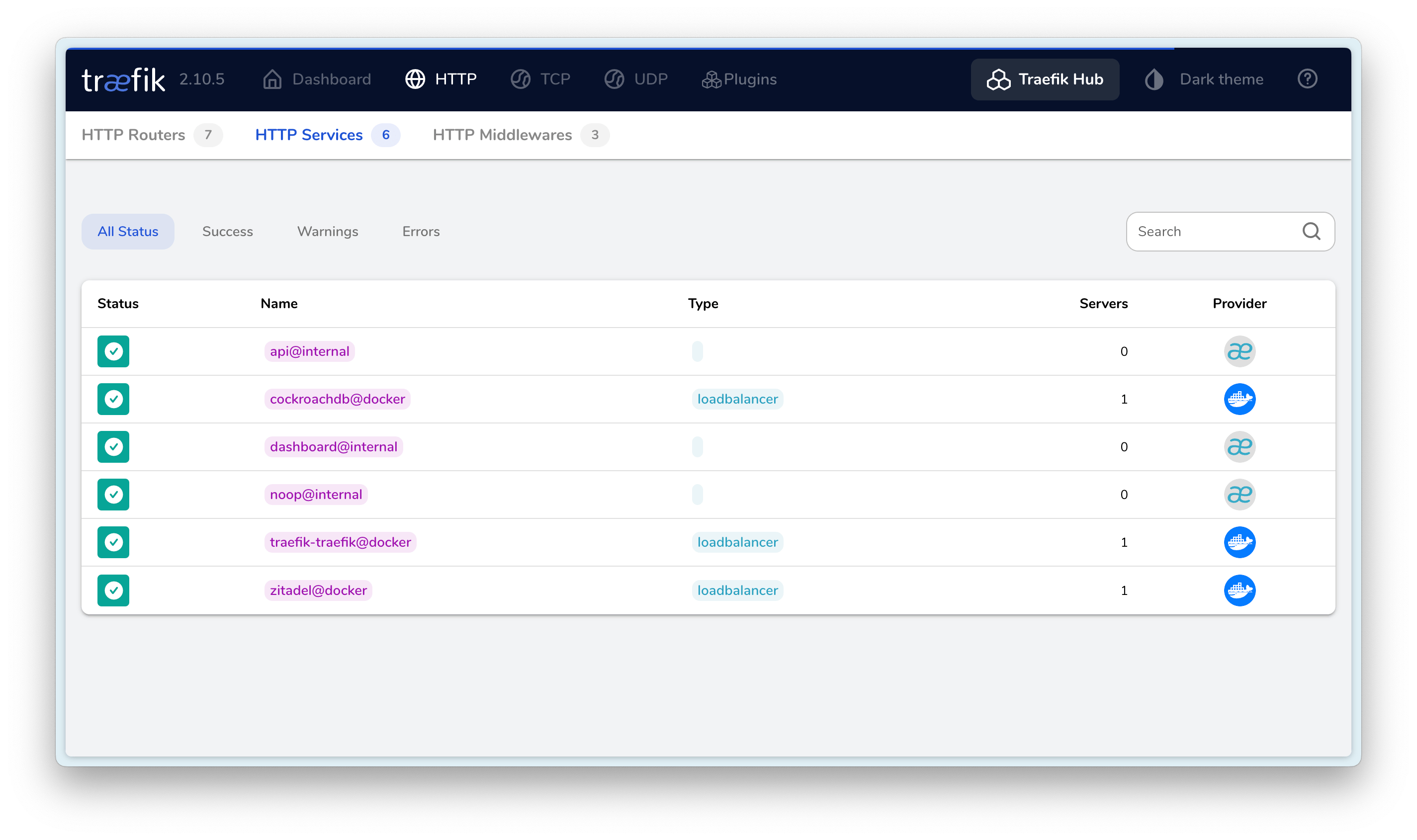
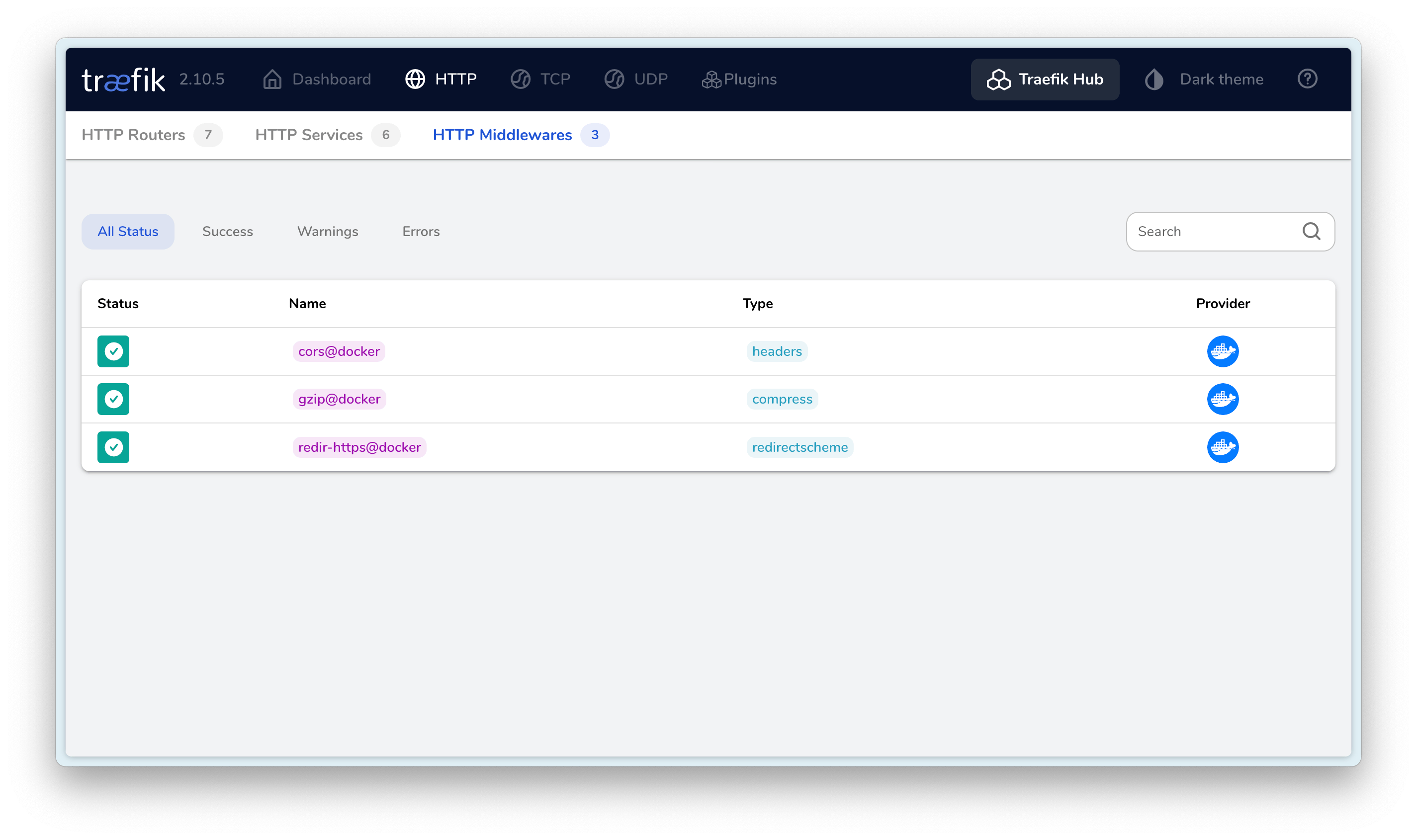
I hope this is helpful, Happy hacking…